HTB - Keeper
User
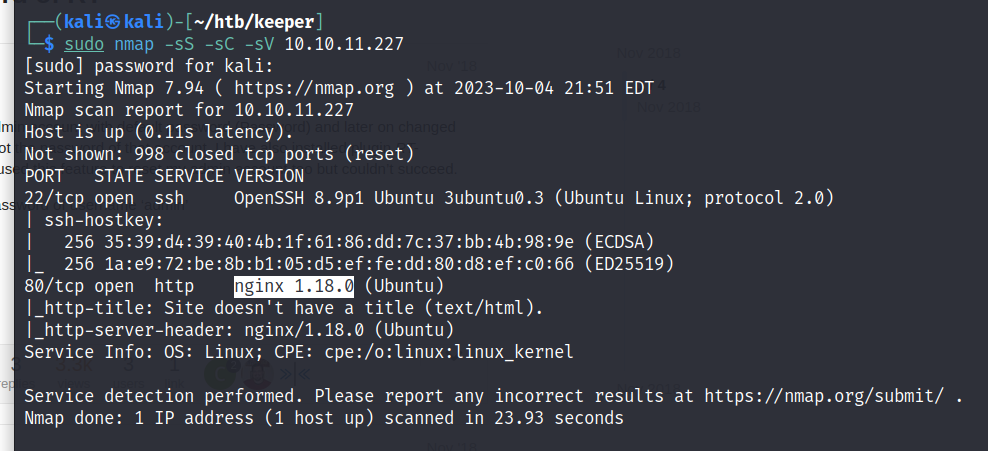
Nmap scan
If we visit the website, we are redirected to tickets.keeper.htb.
Directory and subdomain enumeration did not give us anything.
The website shows a login page for Request Tracker.
As usual, we try default password combinations for weak passwords.
Googling online you will find that the default credentials for RT is root:password
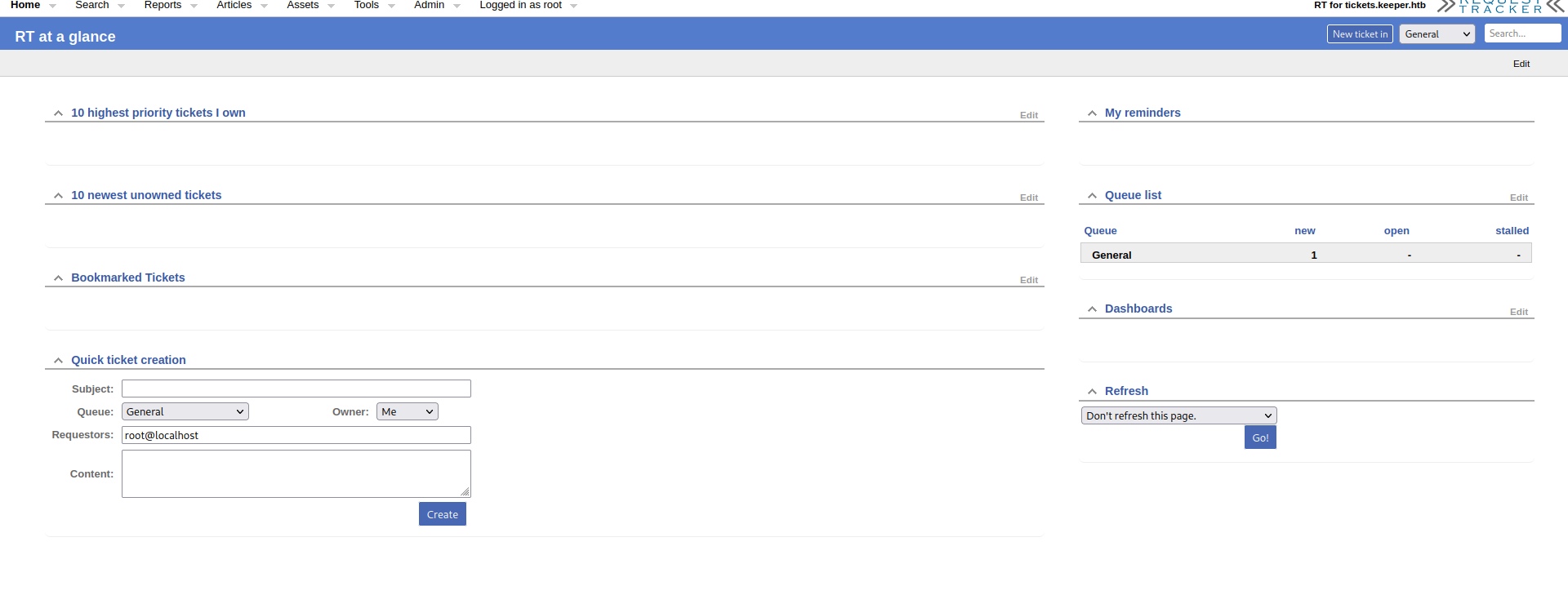
We login to RT, and we get the following page.
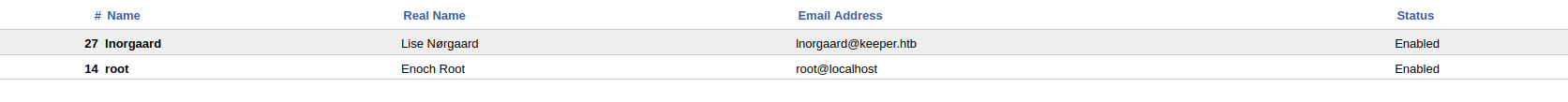
Clicking around, you will find another user in RT.
At this point, I also tried the functionalities in RT. However, creating a new user or ticket returns a CSRF protection error.
Clicking on the user in the panel brings us to the following page.
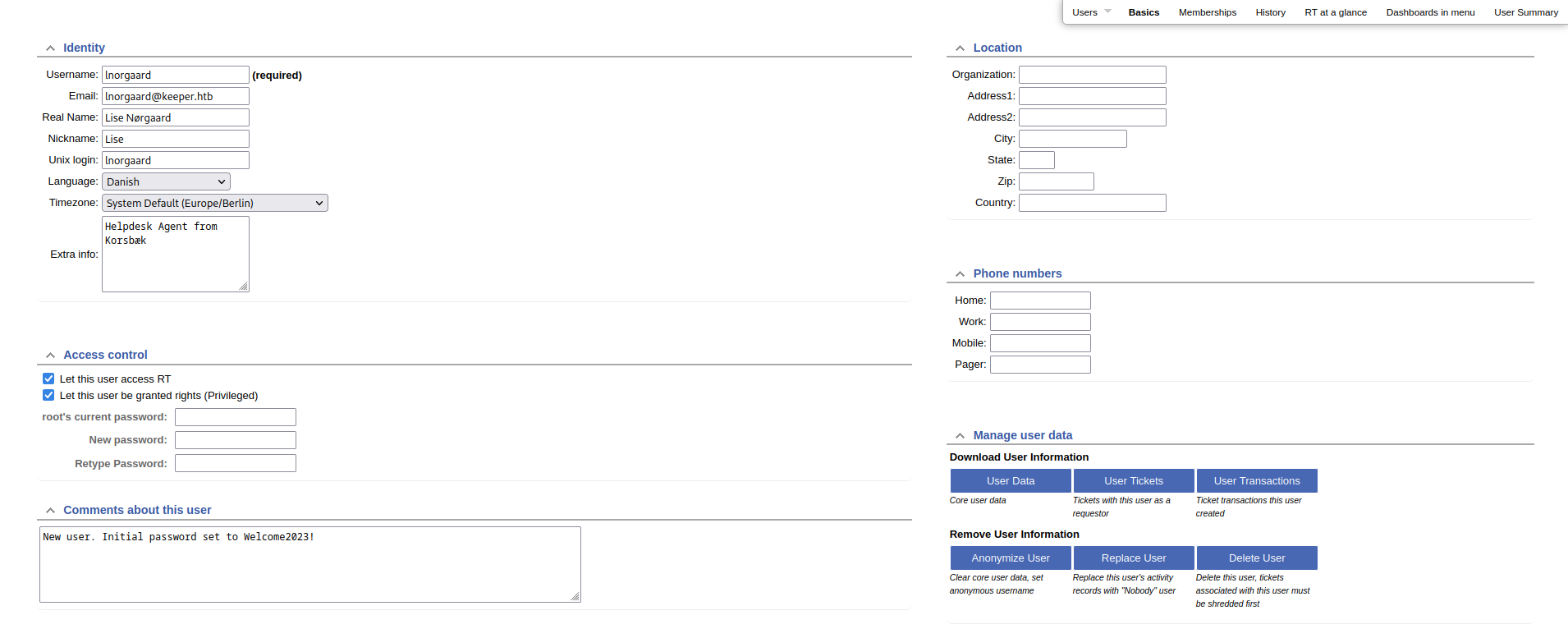
We get the user’s password Welcome2023 and login with SSH.
Root
We find two interesting files in the home directory — keystore.kdbx and keepass.dmp.
Googling for KeePass vulnerabilities online you will stumble upon CVE-2023-32784.
In KeePass 2.x before 2.54, it is possible to recover the cleartext master password from a memory dump, even when a workspace is locked or no longer running. The memory dump can be a KeePass process dump, swap file (pagefile.sys), hibernation file (hiberfil.sys), or RAM dump of the entire system. The first character cannot be recovered. In 2.54, there is different API usage and/or random string insertion for mitigation.
Download the files to our host and run the exploit to recover the master password.
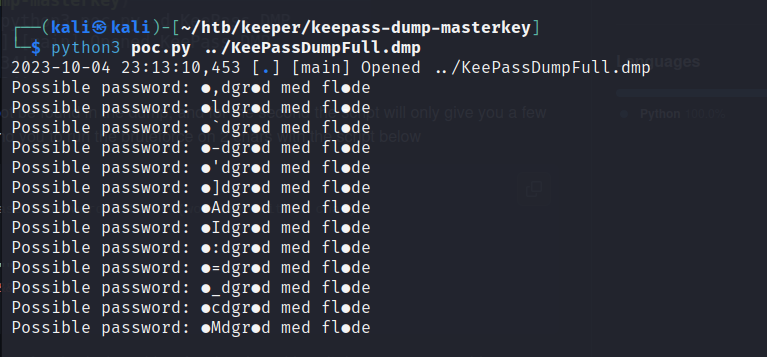
As you can see, there are some weird characters that aren’t showing up in the terminal. This can be caused when characters from unsupported languages are used. Googling ●ldgr●d med fl●de online will return rødgrød med fløde.

Unlock the the .kdbx file with the master password.
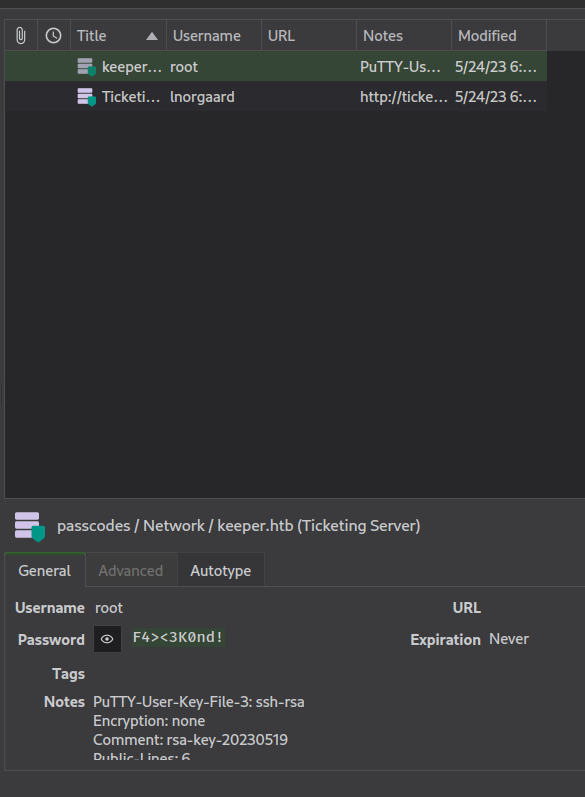
We find the password to root, but SSH login with password was disabled on the box. We have to use the private SSH key in the Notes field.
The key created is a PuTTY private key file, so we will need to use PuTTY for this.
Voila, we are logged in as root.