Introduction to Network Design
Table of Contents
Introduction
I was given this as a homework question, so I’ll be sharing what I learned from researching this topic.
A computer network is a set of computers and network devices connected to communicate with each other. These devices are known as hosts or nodes within the network. The hosts can be interconnected via wired or wireless links, in which they can be arranged in different configurations to form unique topologies. Network design is the process of creating a blueprint for the physical and logical layout of the networking infrastructure to fulfil business needs. As more people gain access to the Internet, companies have incentives to ensure that the infrastructure supporting their services do not fail. There is no definite answer for a network design, each is unique based on the organisation’s needs. Some considerations when designing a network include the use case of the organisation, the number of hosts in the network, the amount of traffic in the network, the cost of setting up and maintaining the infrastructure, and the security of the network.
Network Topologies
Network topology describes the arrangement of hosts in the network and can be divided into two types:
- Physical topology refers to the physical layout of the network. It maps the actual connections in the network and the physical medium used for data transmission.
- Logical topology refers to the paths that a signal takes when travelling through the network. It illustrates how data is transferred from one host to another in the network. In this section, we discuss several topologies, but in practice, the hybrid topology comprising a physical star and logical bus topology is the most commonly used[1].
Point to point
Point-to-point is the simplest topology. There must be a direct link between the hosts for communication. If a host wants to send messages to other hosts, then a physical link must be wired between them. This gets expensive when the number of hosts in the network increases, as many wires will need to be connected. A simple example of point-to-point topology is the cup telephone. The advantages of using point-to-point include ease of set- up as communication only requires connecting a direct link between the two hosts, and fast transmission. The main disadvantage is its bad scalability. If there are many hosts in the network, this will require connecting many wires between hosts which is tedious and expensive. In addition, as communication between the two hosts relies entirely on the single link, point-to-point is prone to failure. In practice, point-to-point is never used.
Bus
Each host in a bus topology is connected to a common link, which is the bus. Therefore, the hosts are directly connected to every other host on the network via the bus. New hosts can be easily added to the network because they only need to be connected to the bus. As all traffic must pass through the common bus, this topology faces congestion problems due to limited bandwidth. Furthermore, because there is only one common link, the bus topology has a single point of failure.
Ring
In a ring topology, the hosts are daisy-chained so that the first host is connected to the last host to form a ring. Data can travel through the ring in either direction. When a node wants to deliver a message to another node in the ring, the message passes through each node until it reaches its destination. The advantage of ring topology is that each node in the ring has equal access to the network even when the number of nodes increases. Because data must pass through each node before reaching its destination, only one node can send data at any given time. This feature significantly reduces the likelihood of packet collisions.
However, the ring topology suffers from the same reliability issues as the bus topology. If one of the nodes in the ring fails, the ring’s structure becomes disconnected. As a result, no alternative communication paths will be available to the nodes, so the entire network is brought down. Adding and removing nodes from a ring topology is also time-consuming. To add or remove from the ring, the existing network has to be suspended, which may not be scalable for large networks.
Star
Star topology is the most common physical topology used in Ethernet switching physical layouts [1]. The host is connected to a central networking device (i.e. a hub, switch, or router) that enables communication with other hosts. As a result, all network traffic must pass through the central node. For example, when host A sends a message to host B, the message is first sent to the central node, which then forwards it to host B. Since the movement of data relies on the central node, this topology suffers from a single point of failure.
However, it has the advantage of being simple and easy to add or modify existing network devices. In addition, the failure of a host does not bring down the network, so other hosts can still communicate with each other. This feature makes star topology more maintainable because the failed node can be pinpointed and repaired while the network is still operational.
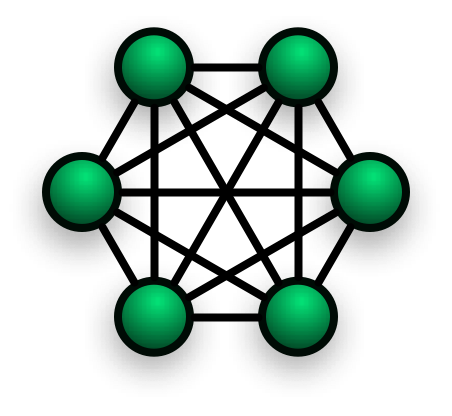
Mesh
In a mesh topology, there are interconnections between each host and other hosts in the network. Therefore, the mesh topology can be represented as a complete graph. For increased reliability, the network has many redundant links between nodes. This allows a source node to find an alternative path to a destination node if a link between them fails. The main disadvantage of using a mesh is the highest cost of installation due to the large number of cables required. The wiring can quickly become complex and difficult to main. Therefore, mesh topology is rarely used for office networks. However, the Internet, which is made up of millions upon millions of interconnected routers, is an example of a network based on mesh topology.
Hybrid
A hybrid topology is a combination of several topologies discussed previously. The idea is to combine the benefits from other topologies to make up for the limitations of an existing topology. For instance, the star bus topology is a common design pattern that combines physical star topology and logical bus topology.
Network Architectures
Client-server architecture
In client-server architecture, the server is a host that is always on standby for requests from other hosts(clients). Client-server architecture is used in web browsers, file transfer protocol(FTP) and email. For example, when a user requests a document from a website through their browsers, a HTTP request is sent to the corresponding web server. The web server receives the HTTP request and responds with the requested document object, which is then parsed and displayed in the user’s browser. To serve many different clients, the IP address of the server must be fixed. Then, clients that want to request data from the server can contact it by including the server’s IP address as the destination address when sending the packet [2].
However, if the web service receives a large amount of traffic, the server can be overwhelmed with HTTP requests from clients. To overcome this problem, web service providers like video streaming services host many servers that are distributed across the globe to respond to client requests quickly.
Peer-to-peer(P2P) architecture
The main difference between P2P and client-server architecture is that P2P does not rely on a centralized server to request data. Instead, communication in P2P architecture is enabled by establishing direct connections between hosts, which are also known as peers. Typically, these peers are computers scattered across the globe that voluntarily participate in the network. Since the service is not controlled by a central entity, P2P provides a decentralized approach to exchange data over a network [2]. P2P is commonly used in high-bandwidth applications like torrenting and video conferencing.
The main advantage of using P2P is its scalability. When a peer requests a file, the file can be retrieved from many other peers located around the world, which then speeds up file transmission for other peers that are requesting the same file. P2P is also inexpensive because the service depends on volunteering peers across the globe so there is no need to invest in dedicated infrastructure. However, security is a concern because it requires direct communication with unknown hosts. Performance and reliability are also inconsistent as the architecture relies on the number of hosting peers and their location. For example, a file may be unavailable when it is needed because there are no available hosting peers online. Performance can also be inconsistent as depends on the number of hosting peers and their location and this also causes reliability problems. For example, a file may not be available when it needs to be requested because there are no available peers online.
References
[1] T. Lammle, Understanding Cisco networking technologies study guide: volume 1. Indianapolis: John Wiley and Sons, 2019.
[2] J. F. Kurose and K. W. Ross, Computer networking: a top-down approach, Seventh edition. Boston: Pearson, 2017.
Credits
- Client-server architecture diagram by Gnome-fs-client.svg: David VignoniGnome-fs-server.svg: David Vignoniderivative work: Calimo (talk) -Gnome-fs-client.svgGnome-fs-server.svg, LGPL, https://commons.wikimedia.org/w/index.php?curid=1578285
- P2P architecture diagram By The 360 Degree - Own work, CC BY-SA 4.0, https://commons.wikimedia.org/w/index.php?curid=116056511




